UK households could face VPN 'ban' after use skyrockets following Online Safety Bill
-
I know how it works, so spare me the explanation. It's not that as easy as you make it out to be. OS and browser companies are actively fighthing "rogue" root CAs and making it harder and harder to use custom CAs, especially on mobile devices.
And for good reason, because by accepting a rogue root CA that's not your own, you're basically undermining the whole trust system that SSL is based on and surrendering all your online privacy and security to the government and your ISP. Whoever has control over that custom root CA has the keys to your online life.
Rolling such a system out countrywide is utter madness.
wrote last edited by [email protected]You obviously didn't know how it works if I had to explain it was already possible. And I am not aware of any mobile device that prevents you installing a new root CA.
And it isn't "madness", it's a completely workable way to offer filtering for people who want it for kids and have no filtering or censorship for anybody else. It is a vastly better option than onerously demanding adults provide their identity to random and potentially adult themed websites where they could be victims of identity theft or extortion
-
You obviously didn't know how it works if I had to explain it was already possible. And I am not aware of any mobile device that prevents you installing a new root CA.
And it isn't "madness", it's a completely workable way to offer filtering for people who want it for kids and have no filtering or censorship for anybody else. It is a vastly better option than onerously demanding adults provide their identity to random and potentially adult themed websites where they could be victims of identity theft or extortion
wrote last edited by [email protected]You obviously didn’t know how it works if I had to explain it was already possible.
If you read my comment properly, you'll see that I wrote: "I know TLS termination and interception and recertifying with custom certificates is a thing"
And it isn’t “madness"
Yes it is. TLS interception should never be normalized because it breaks the chain of trust upon which TLS is based. It can be useful in some situations, like the fortigate firewall where you control the certificate, but ISPs nor the government should be trusted to wield this power over virtually the whole country. It is a very slippery slope.
I am not aware of any mobile device that prevents you installing a new root CA.
On Android, apps can't install their own root CA. The user has to manually download it, then jump through a bunch of hoops and deeply nested menus to install it and in the process ignore all the scary warnings that their communication may be intercepted if they install and trust this certificate, and (at least on Pixel phones) they get a permanent warning in their notification tray that someone may be eavesdropping on them. Which is correct.
It is a vastly better option than onerously demanding adults provide their identity to random and potentially adult themed websites where they could be victims of identity theft or extortion
I'm strongly against government mandated age gates myself, but you're objecting for the wrong reasons. You're not providing your identity to the adult website. You're providing it to the third party identity verifier, who then certifies to the adult website that you are an adult without passing on your actual identity. Keep this in mind when you're arguing against it, because pro-age-gater puritans can use it to undermine your argument.
I object to it first and foremost on principle. I shouldn't have to request permission from a third party or the government to do perfectly normal legal adult things in the privacy of my own home.
Secondly, there is still a privacy problem at the "identity verifier". They may swear up and down that they do not store my identity data, but there is no way to prove that one way or another so I cannot trust that my data can't be leaked through them.
Thirdly, when viewing adult content, I don't want there to be any association between my real identity and the adult content whatsoever, even through a third party, and I don't want there to be anything that uniquely identifies me.
Finally, I object to the (re)demonization of all things sexual in our societies. We seem to be backsliding into puritanism under the guise of protecting the children, while we're doing nothing to protect them from real actually harmful online things that are damaging the younger generations beyond repair.
I have a Gen Z stepson, and all the ways in which he is fucked up by the online world (no attention span, permanent online-ness, no real world friends, always seeking instant gratification, unrealistic expectations about life, an overly materialistic worldview, plenty of manosphere bullshit, ... ) have precious little do do with viewing porn.
-
You're using the default port though, are you not? If the source port were not 1194, a port associated with openvpn, would wireshark still identify this as openvpn traffic?
Wireshark can't but there are other methods, such as checking for the known OpenVPN protocol opcodes in the headers:
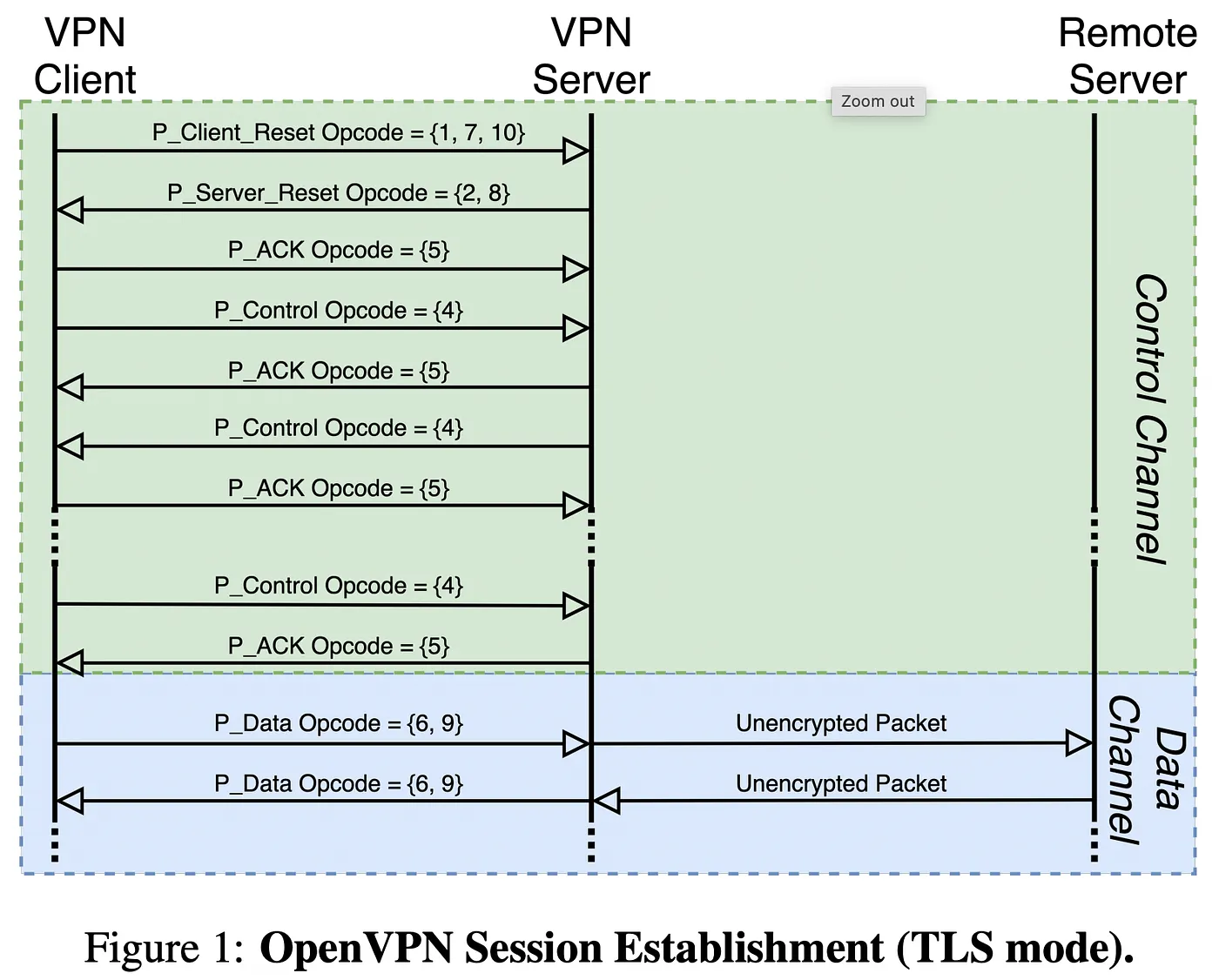
-
Deep packet inspection already happens on encrypted traffic (Fortigate Firewall) so it's eminently possible for filtering software to do the same.
@arc99 please inform yourself about end to end encryption and decryption.
All i say is you haven't understand what is happening on this firewall and what this firewall can do and what the firewall can't do. -
Individual customer VPN providers get banned, corporate VPN providers not banned. It's quite simple really.
Or are you expecting the average Joe to spin up his own VPN server?
And how do you expect that to work on a technical level?
-
@arc99 please inform yourself about end to end encryption and decryption.
All i say is you haven't understand what is happening on this firewall and what this firewall can do and what the firewall can't do.I'm intimately aware about what it can and cannot do. And it can intercept and man in the middles any https traffic
-
I'm intimately aware about what it can and cannot do. And it can intercept and man in the middles any https traffic
@arc99 but end 2 end encryption is not by default https traffic
 ssh / vpn are protocolls ( end 2 end encryption, decryptio) and this firewall can't deep inspect while this protocoll can easy tunnel other tunnels.
ssh / vpn are protocolls ( end 2 end encryption, decryptio) and this firewall can't deep inspect while this protocoll can easy tunnel other tunnels. -
@arc99 but end 2 end encryption is not by default https traffic
 ssh / vpn are protocolls ( end 2 end encryption, decryptio) and this firewall can't deep inspect while this protocoll can easy tunnel other tunnels.
ssh / vpn are protocolls ( end 2 end encryption, decryptio) and this firewall can't deep inspect while this protocoll can easy tunnel other tunnels.I really do not know what you are saying. I have just told you that Fortigate Firewall can and does do deep packet inspection on https connections. It does so by man in the middle proxying. If one filter / proxy can do it then any other could too. There would be ways for kids to circumvent this, e.g via VPN but that is no different than with age verification.
-
I really do not know what you are saying. I have just told you that Fortigate Firewall can and does do deep packet inspection on https connections. It does so by man in the middle proxying. If one filter / proxy can do it then any other could too. There would be ways for kids to circumvent this, e.g via VPN but that is no different than with age verification.
I said (picture) your deep inspection falls short to real end 2 end. You said your firewall can break end 2 end ... nope they can't and never will and you exactly said this in your last post too. (Sidenote -> i can gpg a text and post it public even with https .. for 99% it will be giberish and only the person who got the right key material will be able to read it ) ... so using deep package inspection to identify something you want to protect kids from is just a lie ...
-
I said (picture) your deep inspection falls short to real end 2 end. You said your firewall can break end 2 end ... nope they can't and never will and you exactly said this in your last post too. (Sidenote -> i can gpg a text and post it public even with https .. for 99% it will be giberish and only the person who got the right key material will be able to read it ) ... so using deep package inspection to identify something you want to protect kids from is just a lie ...
I honestly do not know what you are saying. Deep packet inspection through a firewall that does mitm interception demonstrably happens. It is not up for debate.
-
I honestly do not know what you are saying. Deep packet inspection through a firewall that does mitm interception demonstrably happens. It is not up for debate.
@arc99 you still don't understand end 2 end encryption. Yes man in the middle decryption can be done. First for this to happen you need to accept the certificates of the firewall ( which in terms of a home PC you can't force anyone to do ). Second even if you can decrypt the https packets , you can still put an additional layer on top which only you and the reciever has the keys too.
To give you an example you can easy write down a base64 encoded binary blob in any text field on a website. If this binary blob has been encrypted before noone will be able to tell what is inside.
So breaking https is useless if someone really wants to hide informations. So no your deep packet inspection is totally useless. The only thing you know is that someone did put strange stuff in a text on a website.
-
No. They could put it into a review and quietly shitcan this. It's not particularly popular. They just want to say they're protecting kids.
They're spineless and Keir is an authoritarian.
"Oh, i see. You want to help paedophiles do you? Why do you hate children then, hey? Of course keef comes out to help the Jimmy Savile brigade again."
Congratulations, you just lost the media narrative and now all but one paper is going to write about how all the things that hurt every child in the UK is your fault, for the next 3 years. The whole system is compromised and they're passengers, only a little more engaged than we are.
-
"Oh, i see. You want to help paedophiles do you? Why do you hate children then, hey? Of course keef comes out to help the Jimmy Savile brigade again."
Congratulations, you just lost the media narrative and now all but one paper is going to write about how all the things that hurt every child in the UK is your fault, for the next 3 years. The whole system is compromised and they're passengers, only a little more engaged than we are.
Not really the narrative. Reform opposes it and Tories likely will. Only Lib Dems will complain and media ignore them anyway.
Our media are bad, but not that tabloid.
-
Yeah, businesses will not accept this. Remote work and remote connections rely on VPN for ALL KINDS OF SHIT. If you must adhere to some kinds of government compliance, it is even MANDATED BY THE FUCKING GOVERNMENT. Explain to me how the hell that is going to just poof and not cause all kinds of problems.
You don't get it. They will just force VPNs to black list sites. Business users will happily do it because they don't care about porn anyway. Any VPN which doesn't enforce UK laws will be blocked at the ISP level.
-
@arc99 you still don't understand end 2 end encryption. Yes man in the middle decryption can be done. First for this to happen you need to accept the certificates of the firewall ( which in terms of a home PC you can't force anyone to do ). Second even if you can decrypt the https packets , you can still put an additional layer on top which only you and the reciever has the keys too.
To give you an example you can easy write down a base64 encoded binary blob in any text field on a website. If this binary blob has been encrypted before noone will be able to tell what is inside.
So breaking https is useless if someone really wants to hide informations. So no your deep packet inspection is totally useless. The only thing you know is that someone did put strange stuff in a text on a website.
wrote last edited by [email protected]No, YOU don't understand end to end encryption, and you don't understand browsers. You say you could "write down a base64 encoded binary blob on a website". Yes you could and how do you decrypt it? The asnwer is with a key (asymmetric or symmetric) that the recipient must have in memory of the receiving software - the browser that the filter has already intercepted and compromised. So "moar layers" is not protection since the filter could inject any JS it likes to reveal the inner key and/or conversation. It could do this ad nauseum and the only protection is how determined the filter is.
But this is also a nonsense argument just on a practical level. The problem is kids connecting to adult websites, or websites with some adult content. The filter doesn't need to do much - either block a domain outright, or do some DPI to determine from the path what part of the website the browser is calling. The government thinks it reasonable that every single website that potentially hosts adult content should capture proof of identity of adults. I contend that really the issue is kids having access to those websites at all, and that proxies can and would be a far more effective way to control the issue without imposing on adults. No solution is perfect, but a filter is a far more effective way than entrusting some random website with personal information. Only this week somebody found an app that was storing ids in a public S3 bucket compromising all those users. Multiply that by hundreds, thousands of websites all needing verification and this will not be the last compromise by any means.
-
No, YOU don't understand end to end encryption, and you don't understand browsers. You say you could "write down a base64 encoded binary blob on a website". Yes you could and how do you decrypt it? The asnwer is with a key (asymmetric or symmetric) that the recipient must have in memory of the receiving software - the browser that the filter has already intercepted and compromised. So "moar layers" is not protection since the filter could inject any JS it likes to reveal the inner key and/or conversation. It could do this ad nauseum and the only protection is how determined the filter is.
But this is also a nonsense argument just on a practical level. The problem is kids connecting to adult websites, or websites with some adult content. The filter doesn't need to do much - either block a domain outright, or do some DPI to determine from the path what part of the website the browser is calling. The government thinks it reasonable that every single website that potentially hosts adult content should capture proof of identity of adults. I contend that really the issue is kids having access to those websites at all, and that proxies can and would be a far more effective way to control the issue without imposing on adults. No solution is perfect, but a filter is a far more effective way than entrusting some random website with personal information. Only this week somebody found an app that was storing ids in a public S3 bucket compromising all those users. Multiply that by hundreds, thousands of websites all needing verification and this will not be the last compromise by any means.
@arc99 the same way as you did encrypt it ??? with gpg ?
???? the needed certificate are exchanged by for example a matrix / telegram or personal ????
And don't underestimate kids ... Or better asked yourself how did they get porn in the 80s and 90s ??? ( and yes they did )
PS: and honestly imho this hole "protection talk" is totally nonesense or are parent's not anymore capable of protecting their kids? Tell my one reason why a kid < 16 should have access to internet without supervision ? An Emergency Call can still be done without internet.
This hole discussion is like if you would had let a Porn VHS in the 80's unlocked in the living room and your kid unsupervised for hours in the living room. Would have someone called in the 80's to audit if your porn has been stored kids savely you would have gone crazy.
PPS: Just because you don't have statistic's how many kids watched adult content in the 80's or 90's doesn't mean it didn't happen !!!
-
Not really the narrative. Reform opposes it and Tories likely will. Only Lib Dems will complain and media ignore them anyway.
Our media are bad, but not that tabloid.
Why would the tories oppose thier own bill?
I don't think you're fully aware of all the factors here.
-
Why would the tories oppose thier own bill?
I don't think you're fully aware of all the factors here.
Because they've always railed against the nanny state. Kemi is a dreadful populist. It isn't popular.
You're simply making excuses for Keir and anyone that disagrees doesn't understand. Copium.
-
You don't get it. They will just force VPNs to black list sites. Business users will happily do it because they don't care about porn anyway. Any VPN which doesn't enforce UK laws will be blocked at the ISP level.
I just don't believe that method will be as successful as you may think.



