Help with iptables, using nixos setting up a wiregaurd server for friends
-
You need more Excalidraw in your life.
-
Check this project https://github.com/whyvl/wireproxy
-
so my friends wiregaurd config is
{
"[Interface]
Address = 10.0.0.3/24
ListenPort = 51820
PrivateKey = magic numbers[Peer]
PublicKey = magic numbers
PresharedKey = magic numbers
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = magic numbers"
}
So if i understand the article correctly,
i need to change it to
{
"[Interface]
Address = 10.0.0.3/24
ListenPort = 51820
PrivateKey = magic numbers[Peer]
PublicKey = magic numbers
PresharedKey = magic numbers
AllowedIPs = 0.0.0.0/0, ::/0
Endpoint = magic numbers"Split tunneling: Exclude certain traffic from the VPN
PostUp = ip rule add from 192.168.50.0/24 table main
PostDown = ip rule delete from 192.168.50.0/24 table main
}
my friends LAN is 192.168.50.0/0 so im assuming were just trying to tell wireguard that anything within my friends subnet doesnt get routed? which means he will still be able to reach [email protected]? and all of his other traffic will be local to him and go through his router?im confused what "table" and "main" are im assuming its apart of iptables rules? im pretty new to IP tables so forgive me for my lack of understanding. i know its basically a linux purest firewall LMAO,
Then on my server i would edit
This allows the wireguard server to route your traffic to the internet and hence be like a VPN
postUp = '' ${pkgs.iptables}/bin/iptables -A FORWARD -i cavein0 -j ACCEPT ${pkgs.iptables}/bin/iptables -t nat -A POSTROUTING -o enp5s0 -j MASQUERADE ''; # Undo the above preDown = '' ${pkgs.iptables}/bin/iptables -D FORWARD -i cavein0 -j ACCEPT ${pkgs.iptables}/bin/iptables -t nat -D POSTROUTING -o enp5s0 -j MASQUERADE '';And make it like this?
This allows the wireguard server to route your traffic to the internet and hence be like a VPN
postUp = '' ${pkgs.iptables}/bin/iptables -A FORWARD -i cavein0 -j ACCEPT ${pkgs.iptables}/bin/iptables -t nat -A POSTROUTING -o enp5s0 -j MASQUERADE ${pkgs.busybox/bin/ip rule add from 192.168.50.0/24 table main ''; # Undo the above preDown = '' ip rule add from 192.168.1.0/24 table main ${pkgs.iptables}/bin/iptables -D FORWARD -i cavein0 -j ACCEPT ${pkgs.iptables}/bin/iptables -t nat -D POSTROUTING -o enp5s0 -j MASQUERADE ${pkgs.busybox/bin/ip rule delete from 192.168.50.0/24 table main '';Right?
or is step 4 on the client still? its not very clear in the article
thanks for helping out! -
Well you've definitely overcomplicated things by introducing a lot of different variables into the mix. What you've set up is a hat on a hat. An abstraction on top of another abstraction.
Let me break it down and just ask: are you just trying to ensure your friends can only access certain addresses on your network, and you're using Tailscale ACLs for that purpose? It sounds like you just want proper routing security at the edge of your network and are going this route to avoid having to do that maybe?
Tailscale has a place and works great for lots of things, but using it like this is going to cause all kinds of problems eventually. You're basically just advertising a bunch of confused routes to the coordinator like this, and DERP connections will eventually fail or freak out because you're providing multiple paths to different things if I'm reading this right. You're also introducing A LOT of network overhead because of this, and I can forsee a lot of connectivity issues in gaming throughput if that's the main purpose.
-
ok ill try to explain to the best of my ability and simply it.
i no longer want to use tailscale, because of accounts.
i used to use tailscale for the minecraft server
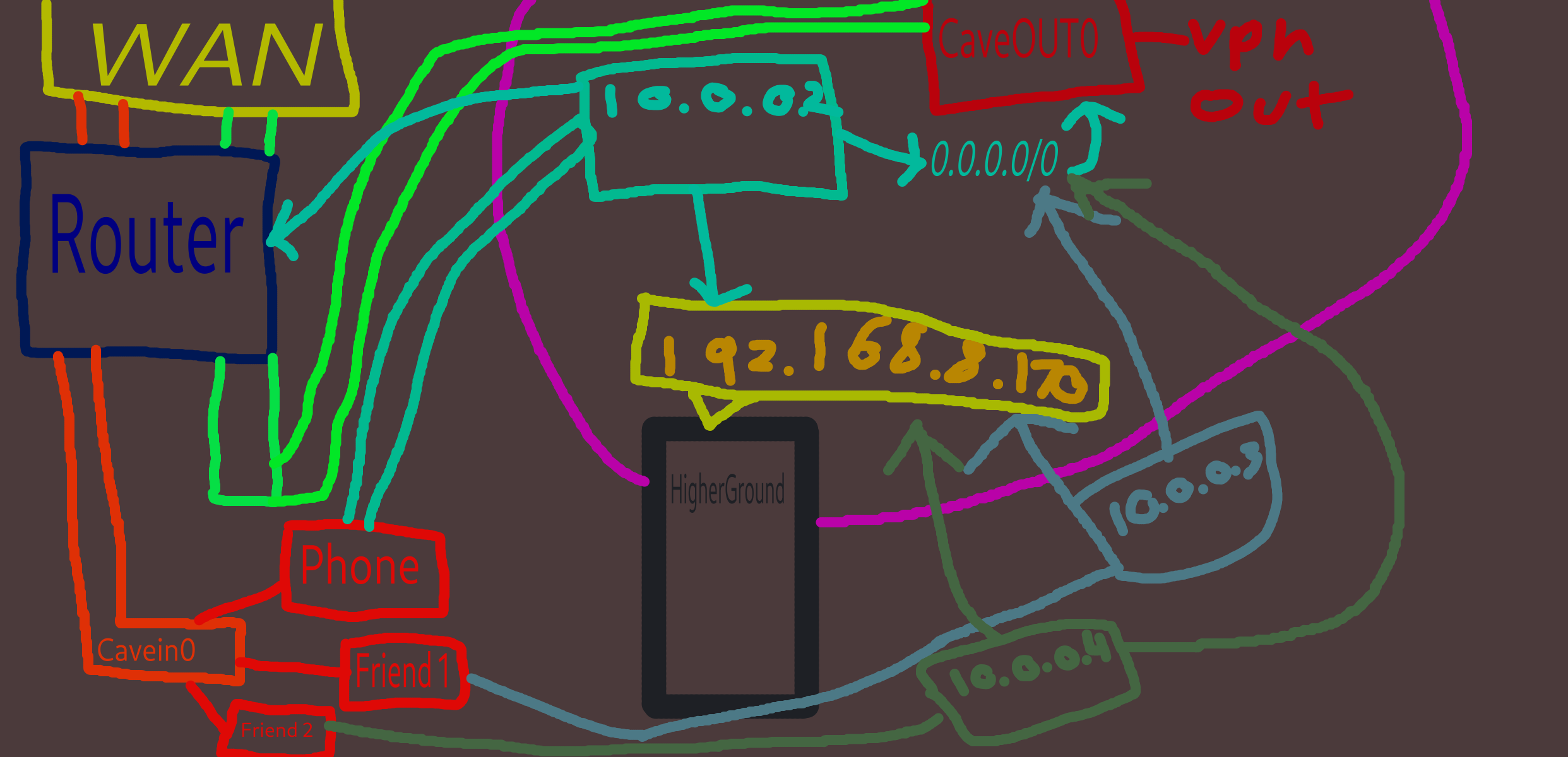
i want my friends to be able to acess only 192.168.8.170 on my local network and all other traffic to not be routed through my vpn but my friends to have acess to there internet on there LAN. example, we can play minecraft on the server on my network and we can be in a group call in signal. meaning friend 1 and 2 are using there internet connection locally, and only 192.168.8.170 being routed.We also had some connectivity issues with tailscale, where friend 1 would be on and friend 2 would lag out of the server randomly. when if we played a game through steam we wouldnt have any connection issues. my friend is also very forgetful and cant log into his tailscale account, which is another reason why i wanna ditch tailscale.
-
Correct me if I'm wrong, but shouldn't this be as easy as setting AllowedIPs to your server ip in your clients configs aswell as your server config?
-
so if i understand this correctly, it runs a docker container to which runs the wireguard server and then you just specify hostname/ip adress for the services, then when sombody tunnels in they have acess to only the services specifide in config file?
if so looks pretty useful!, i just question what happens to the rest of the traffic? is it locally routed in my network or client side?
im not very familiar with proxys, i know what they are but have never really messed with one.
Thanks for sharing -
neat web app!
the drawings kinda suck tho,
but thats just a skill issue on my part
-
so for example, setting 192.168.8.170 on the clients as the only allowed IP aswell as the server would do what i need?
thanks for helping trying to navigate my labyrinth of networking
-
Okay then if Wireguard, you need to punch through your NAT and allow that port access to the world, then to fix your outing issue, you need to look up split-tunneling. That should solve the issues you're seeing if I'm reading this right.
-
To be honest I don't really know, but I know that what you want can easily be solved with SOCKS5 proxy. I think Wireguard and other services are doing pretty much the same. And to be honest you don't need Wireguard for that unless you want to encrypt the traffic. There are also other alternatives to SOCKS5 proxy adding encryption.
In Wireguard you have those Allowed IPs, you can allow only those IPs to be reachable from outside and you can configure them per client if I am not wrong. I think the easiest way would be for you to run those services over Docker, that way each server will have an IP from your docker network and you can isolate the traffic.
My personal suggestion is to spin up a VM, install Debian, Ubuntu, or whatever your poison is, run docker compose or podman compose, spring up a Docker or two and Wireguard and try to achieve what you want. Heck you can even run Wireguard from a container. Once confident with your setup you can migrate it to Nix.
-
No, AllowedIPs should be set to your internal Wireguards IPrange
Here's an example of one of my client configs:
[Interface] Address = 10.8.0.2/32 PrivateKey = [Peer] PublicKey = PresharedKey = Endpoint = 192.168.0.3:51820 AllowedIPs = 10.8.0.0/16Just be careful to not mess up your subnet masks. For example my [Interface] Address ends with /32 because that only leaves 10.8.0.2
In the [Peer] Section i set it to /16 which will allow the client to connect to 10.8.x.x iirc